
welcome iSL
Tez ERP
Protect your digital world with seamless, cutting-edge cybersecurity solutions designed to safeguard your data, systems, and peace of mind.

welcome iSL
Odoo
Protect your digital world with seamless, cutting-edge cybersecurity solutions designed to safeguard your data, systems, and peace of mind.

welcome iSL
Tally Prime
Protect your digital world with seamless, cutting-edge cybersecurity solutions designed to safeguard your data, systems, and peace of mind.

welcome iSL
IT Services
Protect your digital world with seamless, cutting-edge cybersecurity solutions designed to safeguard your data, systems, and peace of mind.
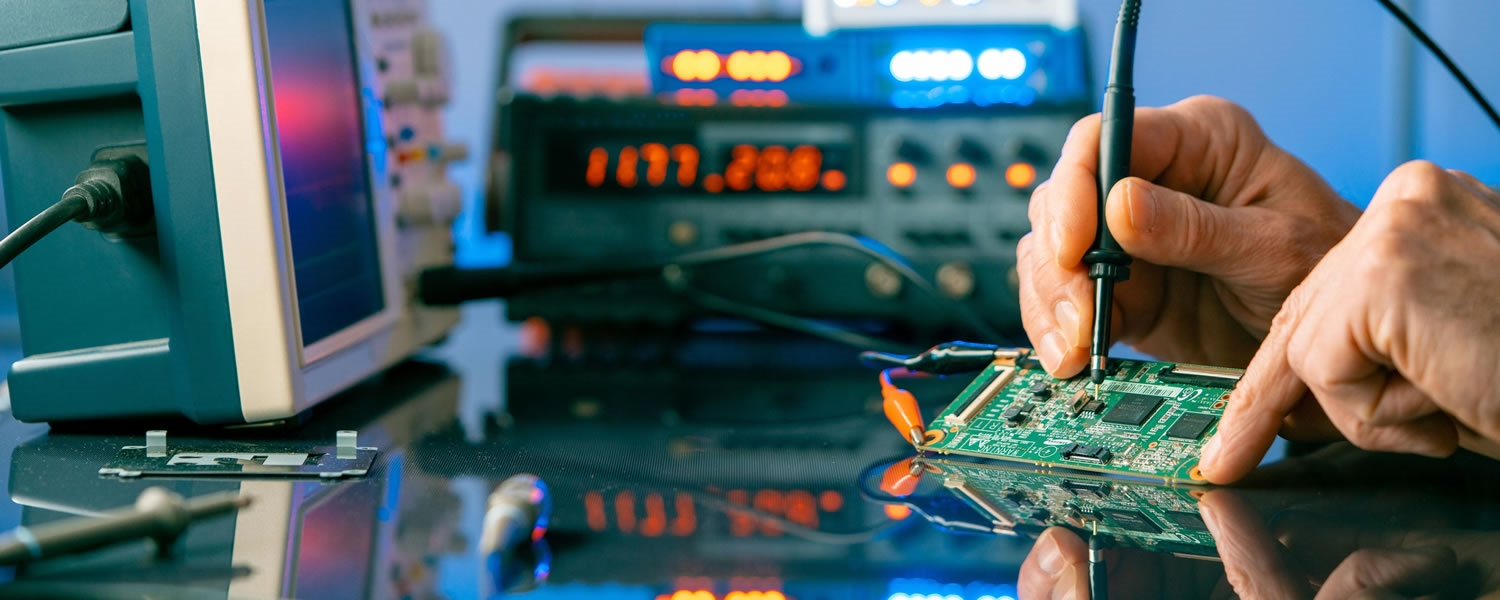
welcome iSL
Live Reparing
Protect your digital world with seamless, cutting-edge cybersecurity solutions designed to safeguard your data, systems, and peace of mind.

welcome iSL
AMC Reparing
Protect your digital world with seamless, cutting-edge cybersecurity solutions designed to safeguard your data, systems, and peace of mind.















